BUU-Web-[极客大挑战 2019]Http
先抓个包看看
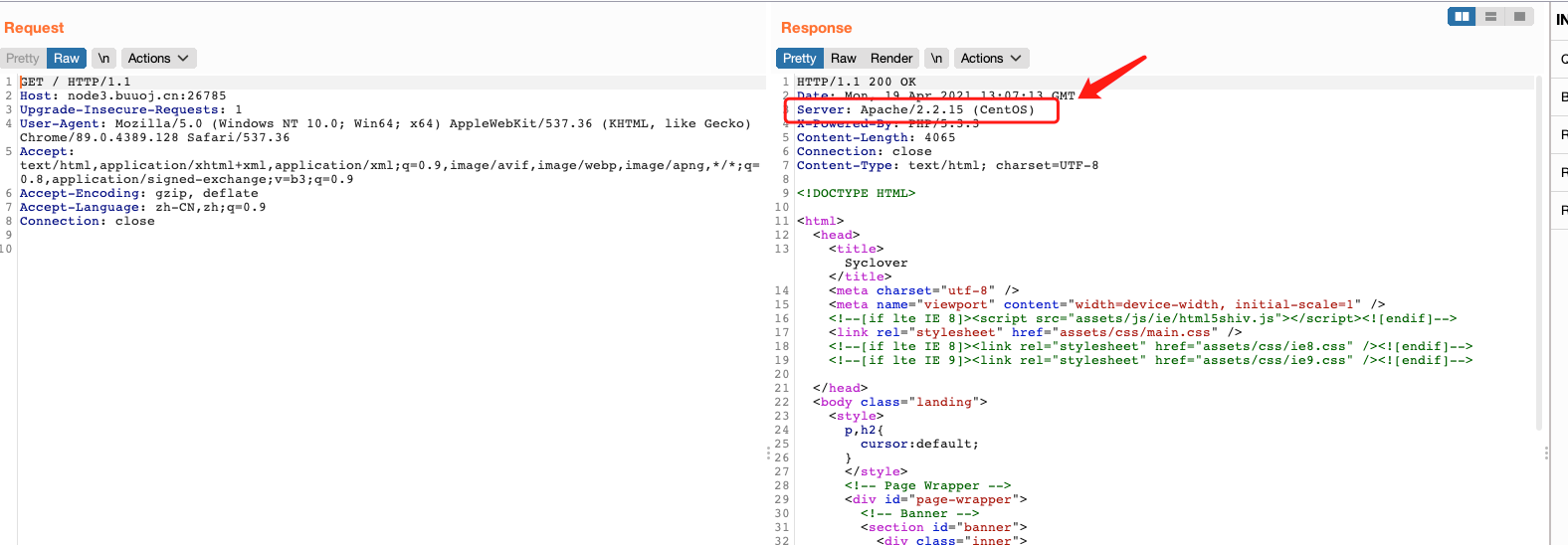
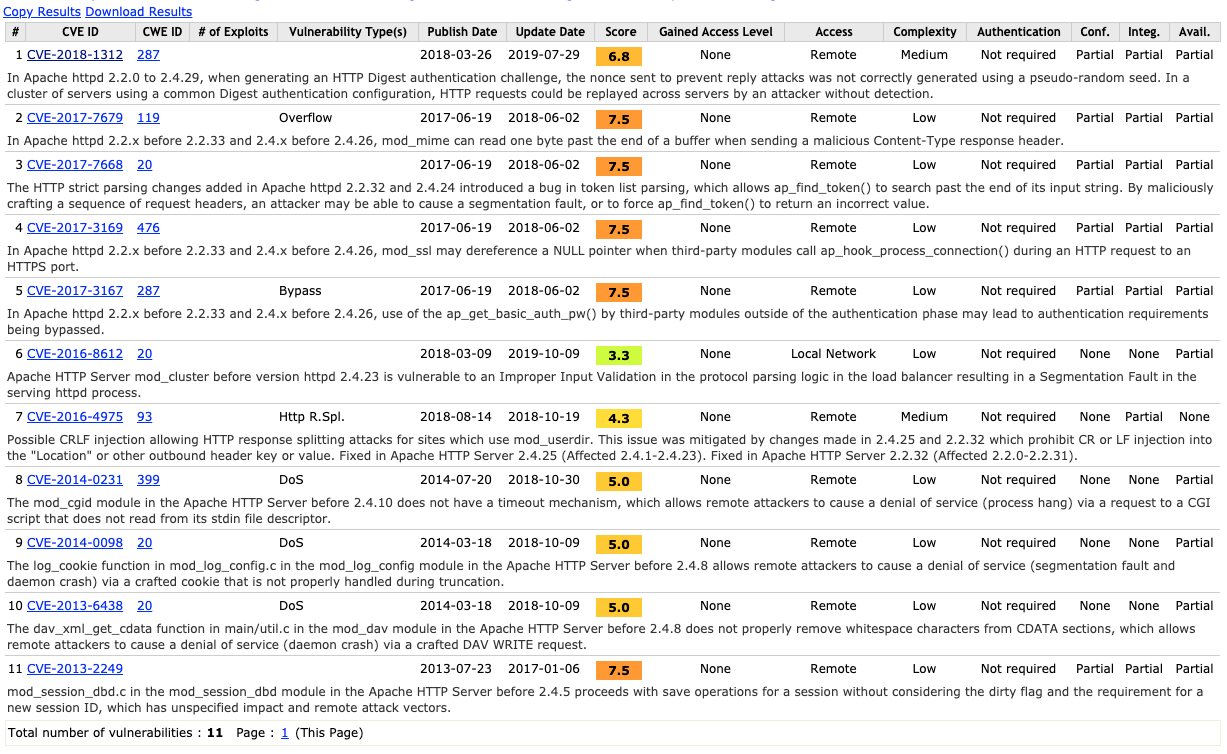
发现当前服务器的版本为Apache/2.2.15 (CentOS),于是便去查了该版本的漏洞
然后通过分析源码发现可以直接查看文件目录
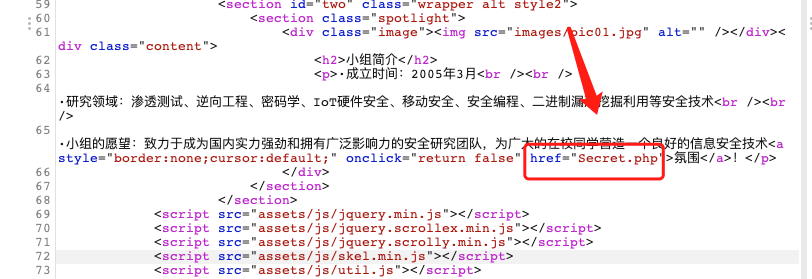
查看了这些目录中的内容并没有发现敏感文件,由于我是条懒狗,没有去利用另外的漏洞,查阅了别人的writeup发现在网页首页源码中就有敏感php文件
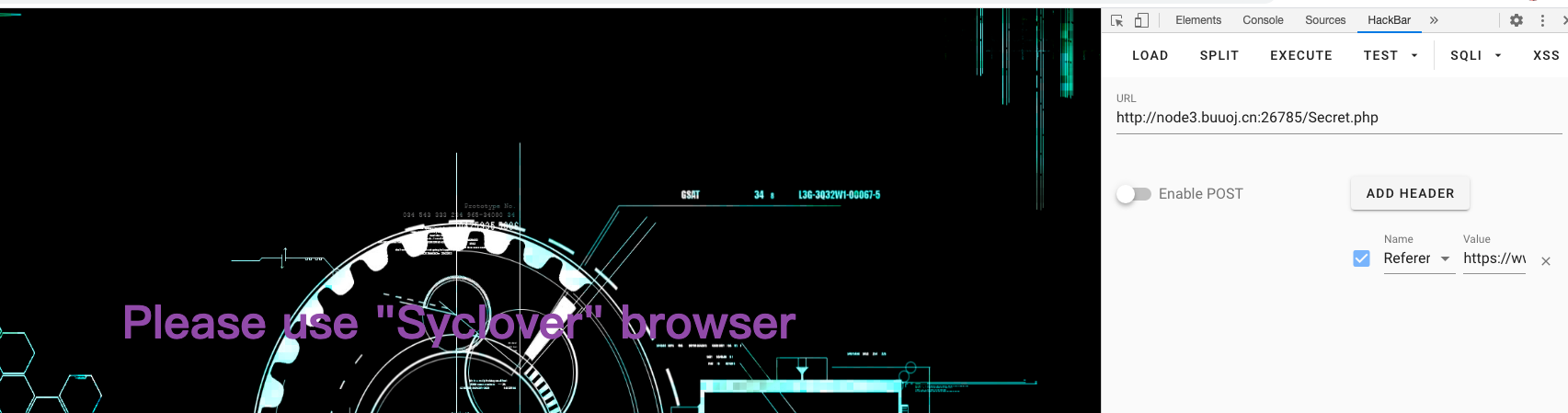
访问后发现需要添加请求头
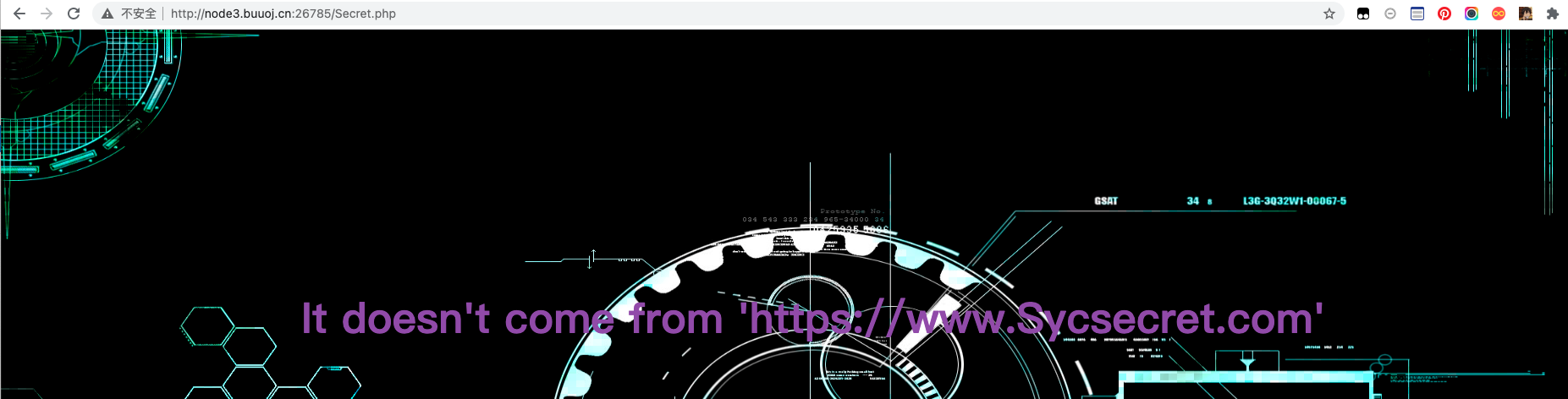

添加第一个请求头 Referer
然后他报出需要“Syclover”浏览器
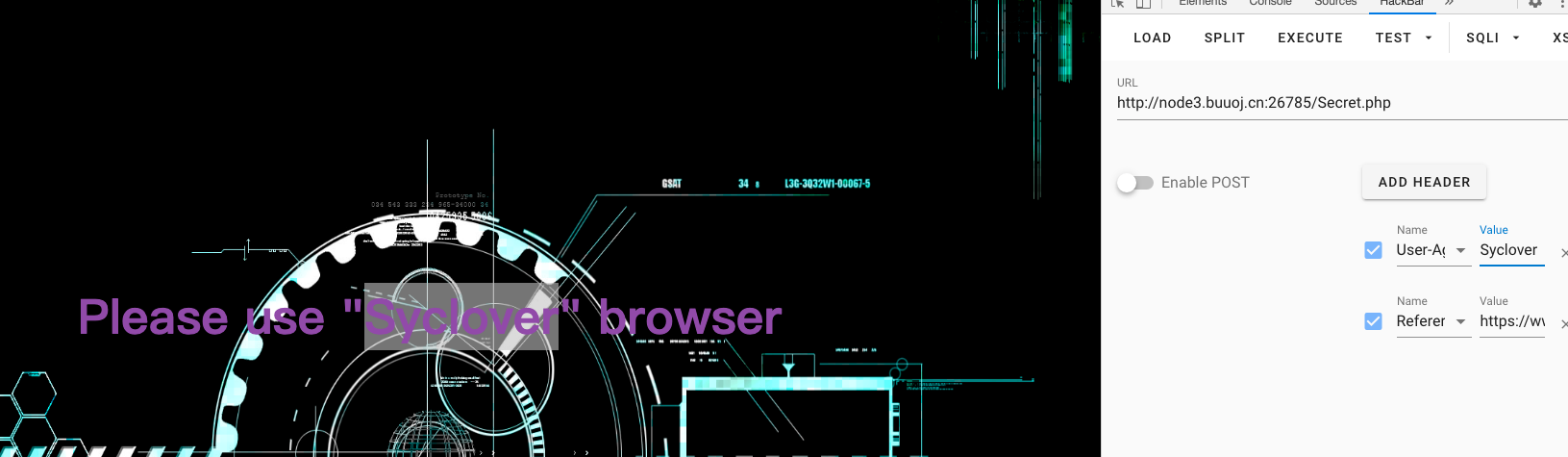
那我们就添加第二个请求头User-Agent
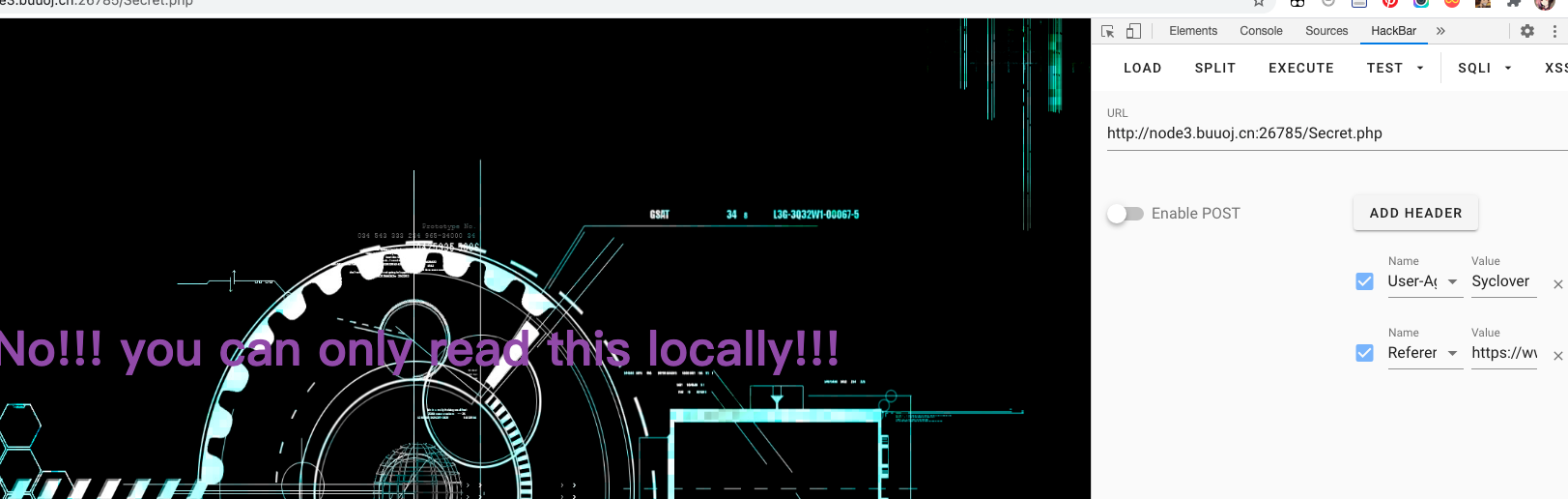
哪知道他又报出需要通过本地访问,这里我就卡了。
通过查阅文档发现可以添加X-Forwarded-For可以伪造本地访问
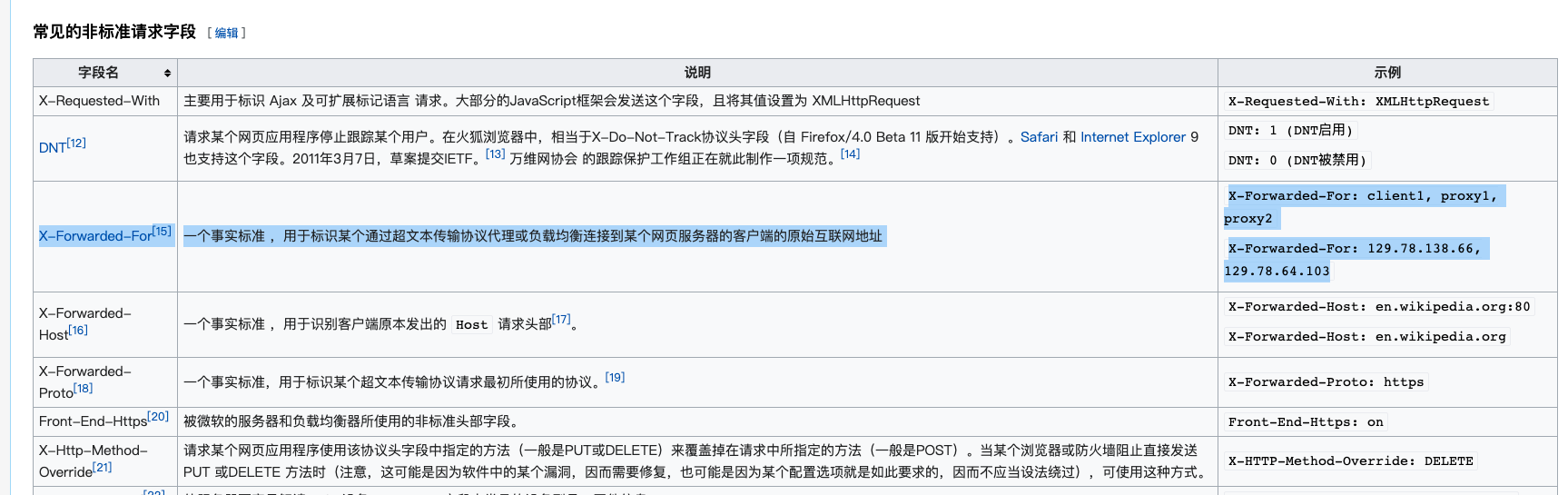
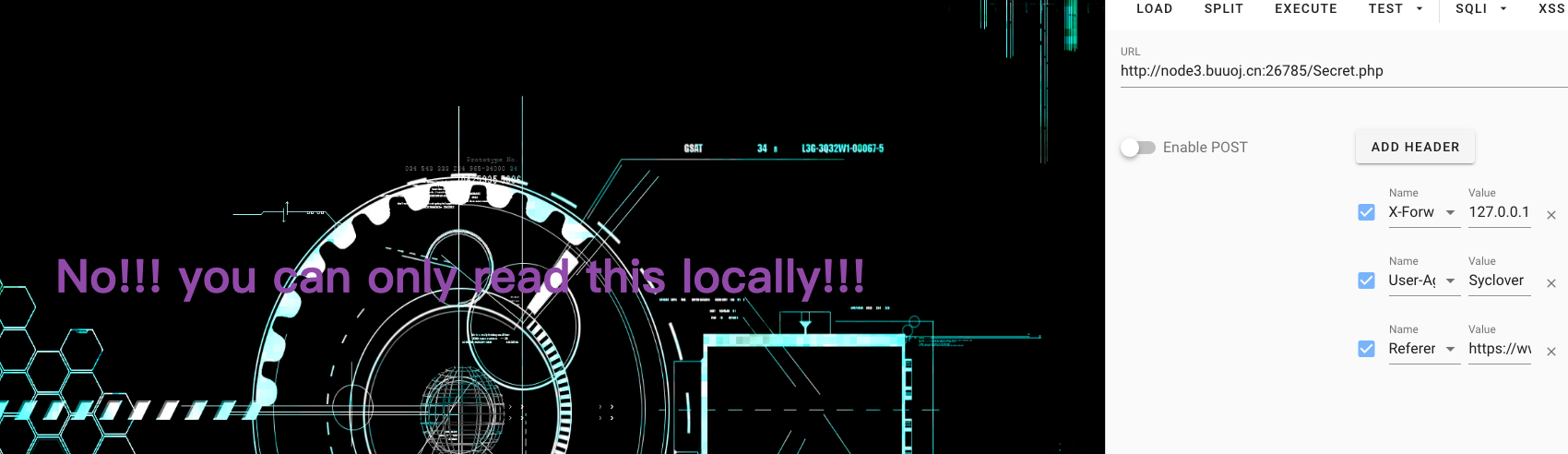
这这里添加第三个请求头X-Forworded-For
最后成功拿到flag


下面进行这道题的技术总结
- 考察了对敏感文件名和敏感字段名对查找
- 对HTTP请求头的了解
- Referer: 来源页面,访问该页面的前一个页面
- User-Agent:浏览器名称常见的如谷歌浏览器(Chrome),火狐浏览器(FireFox),Safari浏览器都有对应的浏览器请求头
- X-Forwarded-For:一个事实标准 ,用于标识某个通过超文本传输协议代理或负载均衡连接到某个网页服务器的客户端的原始互联网地址(Wiki百科 HTTP 头字段)